There are constant level of high attacks and port scans on Linux servers all the time, while a properly configured firewall and regular security system updates adds a extra layer to keep the system safe, but you should also frequently watch if anyone got in. This will also helps to ensure that your server stays free of any program that aims at disrupting its normal operation.
The tools presented in this article are created for these security scans and they are able to identity Virus, Malwares, Rootkits, and Malicious behaviors. You can use these tools make regularly system scans e.g. every night and mail reports to your email address.
1. Lynis – Security Auditing and Rootkit Scanner
Lynis is a free, open source, powerful and popular security auditing and scanning tool for Unix/Linux like operating systems. It is a malware scanning and vulnerability detecting tool that scans systems for security information and issues, file integrity, configuration errors; performs firewall auditing, checks installed software, file/directory permissions and so much more.
Importantly, it doesn’t automatically perform any system hardening, however, it simply offers suggestions that enable you to harden your server.
We will install latest version of Lynis (i.e. 2.6.6) from the sources, using following commands.
# cd /opt/ # wget https://downloads.cisofy.com/lynis/lynis-2.6.6.tar.gz # tar xvzf lynis-2.6.6.tar.gz # mv lynis /usr/local/ # ln -s /usr/local/lynis/lynis /usr/local/bin/lynis
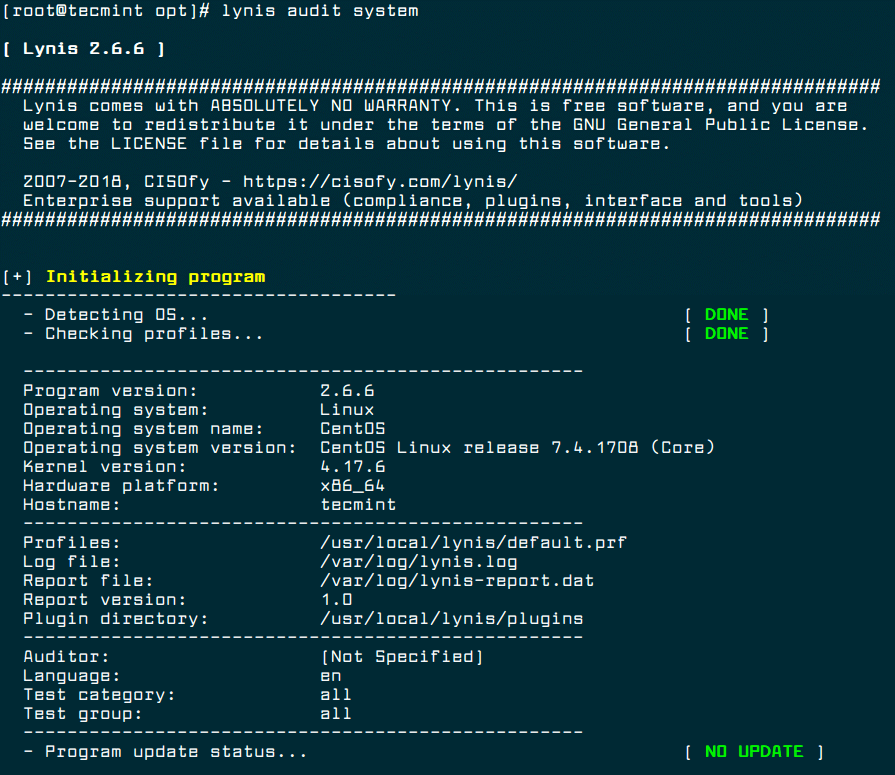
Now you can perform your system scanning with the command below.
# lynis audit system
To make run Lynis automatically at every night, add the following cron entry, which will run at 3am night and send reports to your email address.
0 3 * * * /usr/local/bin/lynis --quick 2>&1 | mail -s "Lynis Reports of My Server" [email protected]
2. Chkrootkit – A Linux Rootkit Scanners
Chkrootkit is also another free, open source rootkit detector that locally checks for signs of a rootkit on a Unix-like systems. It helps to detect hidden security holes. The chkrootkit package consists of a shell script that checks system binaries for rootkit modification and a number of programs that check various security issues.
The chkrootkit tool can be installed using following command on Debian-based systems.
$ sudo apt install chkrootkit
On CentOS-based systems, you need to install it from sources using following commands.
# yum update # yum install wget gcc-c++ glibc-static # wget -c ftp://ftp.pangeia.com.br/pub/seg/pac/chkrootkit.tar.gz # tar –xzf chkrootkit.tar.gz # mkdir /usr/local/chkrootkit # mv chkrootkit-0.52/* /usr/local/chkrootkit # cd /usr/local/chkrootkit # make sense
To check your server with Chkrootkit run the following command.
$ sudo chkrootkit OR # /usr/local/chkrootkit/chkrootkit
Once run, it will start checking your system for known Malwares and Rootkits and after the process is finished, you can see the summary of report.
To make run Chkrootkit automatically at every night, add the following cron entry, which will run at 3am night and send reports to your email address.
0 3 * * * /usr/sbin/chkrootkit 2>&1 | mail -s "chkrootkit Reports of My Server" [email protected]
Rkhunter – A Linux Rootkit Scanners
RKH (RootKit Hunter) is a free, open source, powerful, simple to use and well known tool for scanning backdoors, rootkits and local exploits on POSIX compliant systems such as Linux. As the name implies, it is a rootkit hunter, security monitoring and analyzing tool that is thoroughly inspects a system to detect hidden security holes.
The rkhunter tool can be installed using following command on Ubuntu and CentOS based systems.
$ sudo apt install rkhunter # yum install epel-release # yum install rkhunter
To check your server with rkhunter run the following command.
# rkhunter -c
To make run rkhunter automatically at every night, add the following cron entry, which will run at 3am night and send reports to your email address.
0 3 * * * /usr/sbin/rkhunter -c 2>&1 | mail -s "rkhunter Reports of My Server" [email protected]
4. ClamAV – Antivirus Software Toolkit
ClamAV is an open source, versatile, popular and cross-platform antivirus engine to detect viruses, malware, trojans and other malicious programs on a computer. It is one of the best free anti-virus programs for Linux and the open source standard for mail gateway scanning software that supports almost all mail file formats.
It supports virus database updates on all systems and on-access scanning on Linux only. In addition, it can scan within archives and compressed files and supports formats such as Zip, Tar, 7Zip, Rar among others and more other features.
The ClamAV can be installed using following command on Debian-based systems.
$ sudo apt-get install clamav
The ClamAV can be installed using following command on CentOS-based systems.
# yum -y update # yum -y install clamav
Once installed, you can update the signatures and scan a directory with the following commands.
# freshclam # clamscan -r -i DIRECTORY
Where DIRECTORY is the location to scan. The options -r, means recursively scan and the -i means to only show infected files.
5. LMD – Linux Malware Detect
LMD (Linux Malware Detect) is an open source, powerful and fully-featured malware scanner for Linux specifically designed and targeted at shared hosted environments, but can be used to detect threats on any Linux system. It can be integrated with ClamAV scanner engine for better performance.
It provides a full reporting system to view current and previous scan results, supports e-mail alert reporting after every scan execution and many other useful features.
For LMD installation and usage, read our article How to Install and Use Linux Malware Detect (LMD) with ClamAV as Antivirus Engine.
That’s all for now! In this article, we shared a list of 5 tools to scan a Linux server for malware and rootkits. Let us know of your thoughts in the comments section.

What does it mean when ClamAV doesn’t find any infections but reports many errors?
None of the commands is doing anything.
Update for those reading this years later.
The cron job for rkhunter won’t work. It will get stuck waiting for someone to hit enter on the keyboard.
The correct cronjob would be:
This will make the job run at 4:30 AM and you can view the log at /var/log/rkhunter.log
If you want emails sent to you edit the following line in /etc/rkhunter.conf:
Out of the box rkhunter usually gives some false positives so you need to take some time to configure it to whitelist certain items on your system or you will get an email every day saying there is a problem.
Is there an easy way to scan for malware in hardware/firmware?
somehow the link did not get posted correctly for debcheckroot:
https://www.elstel.org/debcheckroot/Currently, the best tool out there to check for rootkits: Ddebcheckroot.
It should work for Debian and Ubuntu. It can detect any previously unknown rootkit not present in any database!
After 10 years on Linux with no discernible virus, trojan or malware I thought I’d give the above a trial run. Hoping for another decade of confidence in my Linux systems.
I will run all of these on a regular basis to ensure no intrusions.
Cynical note: When windows finally dies, the security industry may turn their attention to Linux and macOS. Infections will follow and the industry will magically have solutions for us to purchase.
Positive note: Windows won’t die, infecting systems will become a toy of the past.
Windows must die, along with capitalism
Windows = Socialism
Linux = Capitalism
Hello,
Trying to get my Lexmark 2600 series printer to run. I downloaded lexmark 2600 server software: lexmark-08z-series-driver-1.0-1.i386.deb.sh (not sure about sh). This installation requires root (administration) privileges in order to continue. I am sole user but don’t believe I got root privileges. Hope you can advise, thanks
@Peter,
To install software on Linux, you must be root or have root privileges like sudo.
Do you install one in particular over others or install them all?
@Craig
You can actually run more than one, on the same system or more so install all of them.