A Pre-Shared Key (PSK) or also known as a shared secret is a string of characters that is used as an authentication key in cryptographic processes. A PSK is shared before being used and is held by both parties to the communication to authenticate each other, usually before other authentication methods such as usernames and passwords are applied.
It is commonly used in different types of Virtual Private Network (VPN) connections, wireless networks in a type of encryption known as WPA-PSK (Wi-Fi Protected Access Pre-Shared Key) and WPA2-PSK, and also in the EAP (Extensible Authentication Protocol Pre-Shared Key), and many others authentication mechanisms.
In this article, we will show you different ways to generate a strong Pre-Shared Key in Linux distributions.
1. Using OpenSSL Command
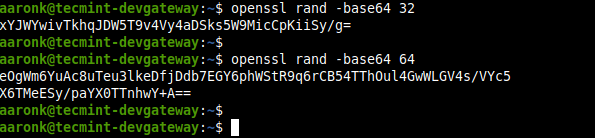
OpenSSL is a well-known and widely-used command-line tool used to invoke the various cryptography functions of OpenSSL’s crypto library from the shell. To generate a strong PSK use its rand sub-command which generates pseudo-random bytes and filter it through base64 encodings as shown.
$ openssl rand -base64 32 $ openssl rand -base64 64
2. Using GPG Command
GPG is a command-line tool to provide digital encryption and signing services using the OpenPGP standard. You can use its --gen-random option to generate a strong PSK and filter it through base64 encoding as shown.
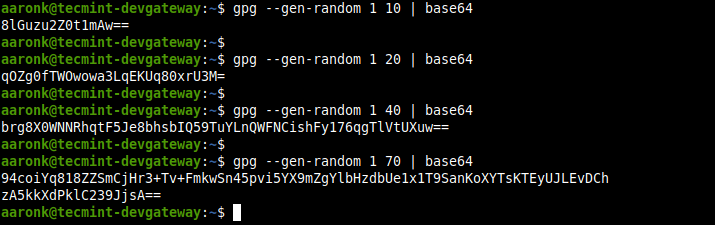
In the following commands, 1 or 2 is the quality level and 10, 20, 40, and 70 are the character counts.
$ gpg --gen-random 1 10 | base64 $ gpg --gen-random 2 20 | base64 $ gpg --gen-random 1 40 | base64 $ gpg --gen-random 2 70 | base64
3. Using Pseudorandom Number Generators
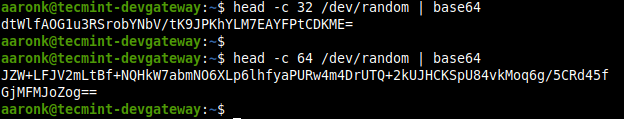
You can also use any of the pseudorandom number generators in Linux such as /dev/random or /dev/urandom, as follows. The -c option of the head command helps to generate the number of characters.
$ head -c 35 /dev/random | base64 $ head -c 60 /dev/random | base64
4. Using date and sha256sum Commands
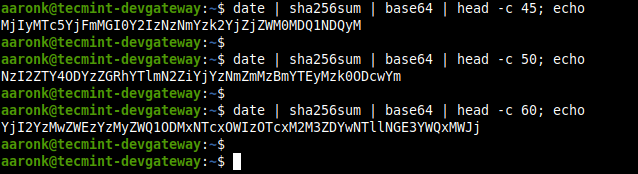
The date and sha256sum command can be combined to create a strong PSK as follows.
$ date | sha256sum | base64 | head -c 45; echo $ date | sha256sum | base64 | head -c 50; echo $ date | sha256sum | base64 | head -c 60; echo
The above are some of the many ways of generating strong Pre-Shared Key in Linux. Do you know of any other methods? If yes, share it with us via the feedback form below.



My favorite, because you can choose which characters are used:
This will create a 64 character alphanumeric PSK.
Replace a-zA-Z0-9 with another list of characters and ranges to control which characters occur, and replace 64 with another number to control length.
e.g.
8 lower-case letters
16 handwriting-unambiguous alphanumeric characters
64 alphanumeric characters and all non-space printable ascii symbols (\ escapes the ! for the shell)
64 URL-safe characters (\ escapes the ()'!*; for the shell)
@Carlo,
Thanks for the tip, hope these commands helpful to our readers…
Note that using “date” to generate keys is *not* secure.
date prints strings like “Sun Dec 6 18:05:53 PST 2020”. Since this string changes once per second, in any given day there are only 86,400 potential keys. This is a tiny number of keys that is easy for an attacker to brute force. In comparison “openssl rand -base64 32” has 256^32 potential keys, a vastly larger number that is difficult to brute force (115,792,089,237,316,195,423,570,985,008,687,907,853,269,984,665,640,564,039,457,584,007,913,129,639,936)
“4. Using date and sha245sum Commands”
should read:
“4. Using date and sha256sum Commands”
It’s confusing enough without hurting the noob’s brain even more! ;-)
Thank-you.
@Nooby,
Thanks, corrected the command in the article.