When installing software on a Linux system is usually a smooth ride. In most cases, you would use a package manager such as apt, dnf, or Pacman to install it securely from your distribution’s repositories.
In some instances, however, a software package may not be included in the distribution’s official repository. In such scenarios, one is compelled to download it from the vendor’s website. But how sure are you that the software package wasn’t tampered with? This is the question we will seek to answer. In this guide, we focus on how to verify the PGP signature of a downloaded software package in Linux.
PGP (Pretty Good Privacy) is a cryptographic application used for encrypting and signing files. Most software authors sign their applications using the PGP program for instance GPG (GNU Privacy Guard).
GPG is a cryptography implementation of OpenPGP and it enables secure transmission of data and can also be used to verify the integrity of the source. In a similar fashion, you can leverage GPG to verify the authenticity of downloaded software.
The verification of the integrity of downloaded software is a 5-step procedure that takes the following order.
- Downloading the public key of the software’s author.
- Checking the key’s fingerprint.
- Importing the public key.
- Downloading the Signature file of the software.
- Verify the signature file.
In this guide, we will use Tixati – a peer-to-peer file sharing program – as an example to demonstrate this. Already, we have downloaded the Debian package from the Offical download page.
Verify the PGP Signature of Tixati
Right off the bat, we are going to download the Author’s Public key that is used for verifying any releases. The link to the key is provided at the bottom of the Tixati downloads page.
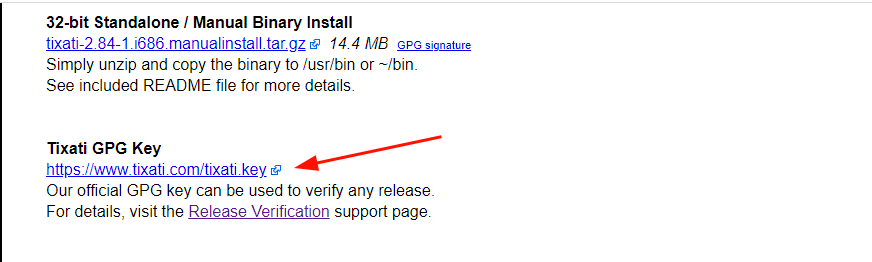
On the command line, grab the Public key using the wget command as shown.
$ wget https://www.tixati.com/tixati.key
Check the Public key’s Fingerprint
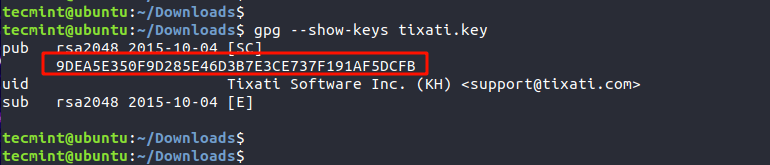
Once the key is downloaded, the next step is to check the Public key’s fingerprint using the gpg command as shown.
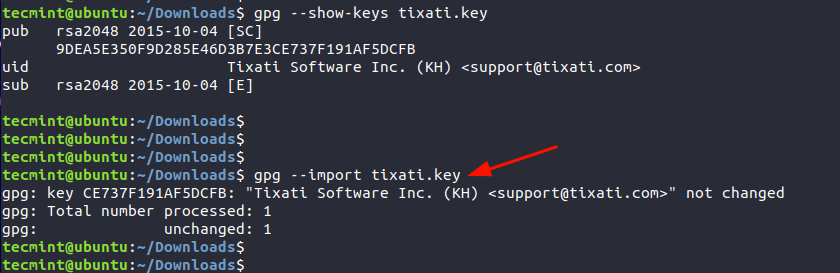
$ gpg --show-keys tixati.key
The highlighted output is the fingerprint of the public key.
Import the GPG Key
Once we have checked the key’s public fingerprint, we will import the GPG key. This only needs to be done once.
$ gpg --import tixati.key
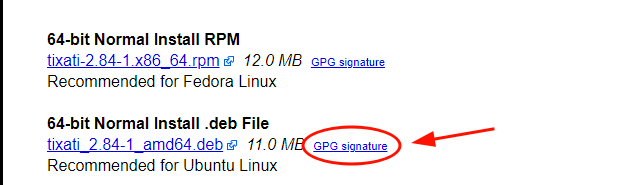
Download Signature File of the Software
Next, we will download the PGP signature file which is just adjacent to the Debian package as indicated. The signature file bears the .asc file extension.
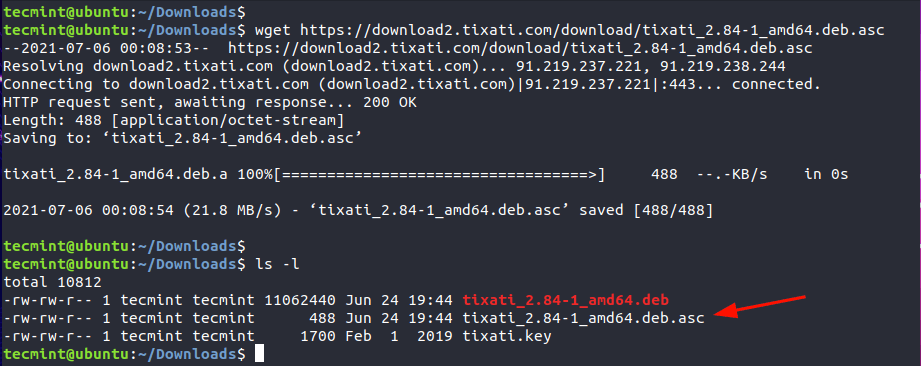
$ wget https://download2.tixati.com/download/tixati_2.84-1_amd64.deb.asc
Verify the Signature File
Lastly, verify the integrity of the software using the signature file and against the Debian package as shown.
$ gpg --verify tixati_2.84-1_amd64.deb.asc tixati_2.84-1_amd64.deb
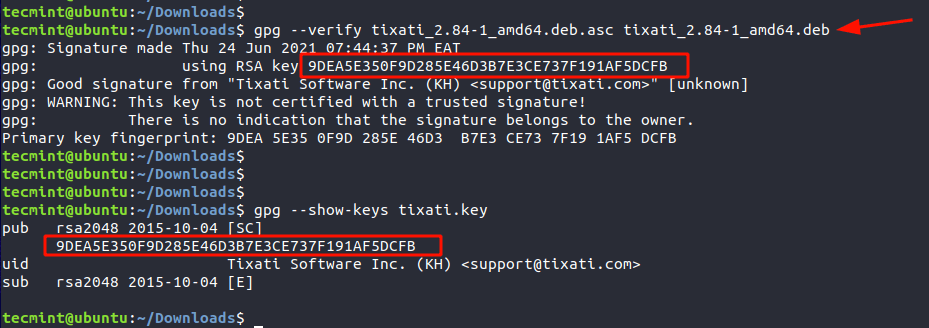
The third line’s output confirms that the Signature is from the software’s author, in this case, Tixati Software Inc. The line above provides the fingerprint which matches the fingerprint of the Public key. This is confirmation of the PGP signature of the software.
We hope that this guide provided insights into how you can go about verifying the PGP of a downloaded software package in Linux.