Brief: In this guide, we will discuss the common use cases of SSH. We will also discuss commonly used SSH configurations that can be used in day-to-day life to boost your productivity.
Secure Shell (SSH) is a widely adopted network protocol, which allows us to interact with remote hosts in a secure way. It provides security by encrypting all communication between them.
How to Use SSH Command in Linux
In this section, we will discuss some of the popular use cases of the SSH protocol.
Connect to Remote Linux Host
There are various ways to interact with remote Linux hosts using protocols such as telnet, ftp, netcat, etc. However, these are not secure due to the absence of encryption. We can use the SSH protocol to allow secure communication between the hosts.
We have to use an SSH client to interact with the remote host. There are plenty of GUI and CLI-based clients available for Linux. However, throughout this guide, we will use a command line utility called ssh. By default, the ssh utility is available on most Linux distributions.
The syntax of the SSH command is as follows:
$ ssh [OPTIONS] [COMMANDS] [ARGS]
Here, the square brackets ([]) represent the optional arguments whereas angular brackets (<>) represent the mandatory arguments.
Let’s connect to the remote host using the ssh client:
$ ssh -l root 192.168.19.130
In this example, we specified the login name using the -l option and the destination is 192.168.19.130. The SSH connection gets established after entering the correct password. Now onwards, we can execute the commands on the remote host just like the local system.
# hostname
To terminate the session, we can use the exit command or ctrl+D key combination.
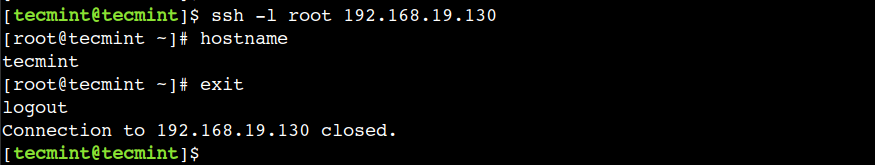
It is important to note that we have to authenticate with the remote host for each new session. To avoid entering passwords each time, we can set up an SSH passwordless login.
Execute Commands on the Remote Host
In the previous section, we saw how to establish a connection with a remote host, which is suitable only when we are going to use the remote host for a longer duration. Sometimes, we just need to execute one or two commands on the remote host. In such cases, we can execute those commands without creating a long-term session.
Let’s execute the hostname command on the remote host:
$ ssh -l root 192.168.19.130 hostname
In a similar way, we can execute multiple commands on a remote Linux machine:
$ ssh -l root 192.168.19.130 'hostname; pwd'
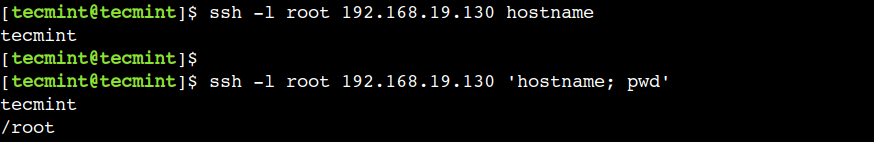
It is important to note that, the commands must be enclosed within the quotes and separated by the semi-colon (;) character. If you want to run commands on multiple remote Linux hosts, read our article – Pssh – Run Commands on Multiple Remote Linux Hosts.
Execute Script on the Remote Host
Similar to the commands we can also execute a local script on the remote host. Let’s understand this with an example.
First, create a simple shell script on a local machine with executable permissions on it:
$ cat script.sh hostname pwd
Now, let’s execute it on the remote host:
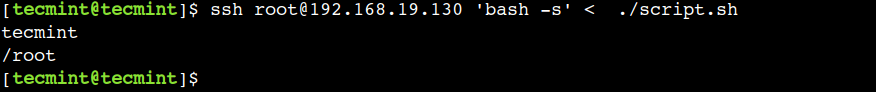
$ ssh [email protected] 'bash -s' < ./script.sh
In this example, we have used the -s option of the bash to read the script from the standard input.
Copy Files Between the Hosts
We work with the files and directories very often. One common operation users perform is copying directories and files. Just like local machines, we can copy files and directories between the remote hosts using the scp command, which copies the files securely using the SSH protocol.
Let’s copy the script.sh file to the /tmp directory of the remote host:
$ scp script.sh [email protected]:/tmp
Now, verify that file has been copied:
$ ssh [email protected] 'ls /tmp/script.sh'
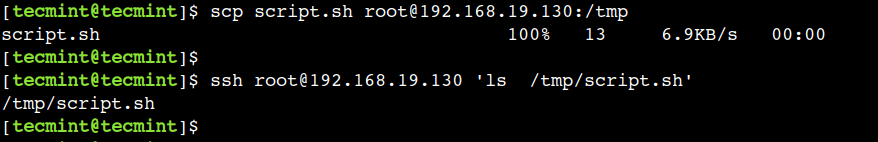
In a similar way, we can use the scp command to copy the directories. However, we have to use the -r option with the command.
Enable Compression for SSH
SSH supports data compression using the gzip compression algorithm, which compresses all possible data streams such as stdin, stdout, stderr, and so on. This option comes in very handy while using slow network connections.
We can enable the compression on SSH using the -C option:
$ ssh -C -l root 192.168.19.130 'hostname'
Enable Verbose Mode for SSH
Linux users often need to debug SSH sessions to investigate various SSH connection and configuration-related issues. In such cases, we can enable the verbose mode that prints the debug logs of the current session.
Let’s enable the verbose mode using the -v option:
$ ssh -v -l root 192.168.19.130 hostname
In addition to this, we can increase the verbosity level by using the multiple -v options.
-v– sets the verbosity level to 1 and provides details about the client-side activities.-vv– sets the verbosity level to 2 and provides details about the client and server-side activities.-vvv– sets the verbosity level to 3 and provides more detailed information about the client and server-side activities.
The maximum verbosity level supported by SSH is 3. Let’s see this in action:
$ ssh -vvv -l root 192.168.19.130 hostname
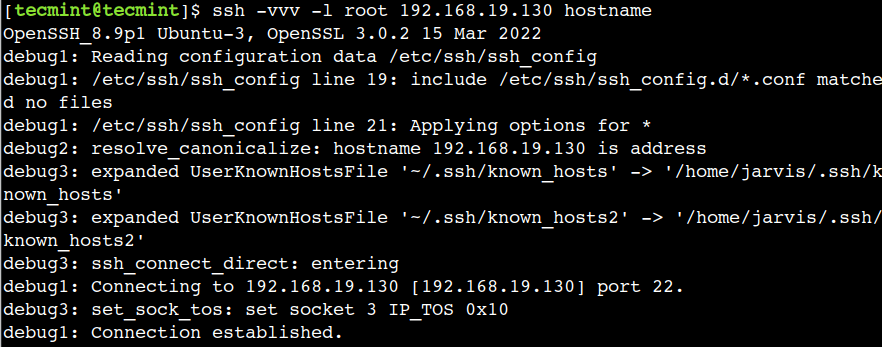
In the above example, debug1 represents the debug message enabled by the verbosity level 1. Similarly, debug2 and debug3 represent the debug messages enabled by the verbosity levels 2 and 3 respectively.
Escape Sequences in SSH
We can use escape sequences with the SSH to manage the client terminal sessions. Let’s discuss commonly used escape sequences with the appropriate use cases.
Suspending SSH Session
Sometimes, we have to perform a few activities on the local machine without terminating the current SSH session. In such a scenario, we can suspend the current session using the ~ + ctrl + z key sequence.
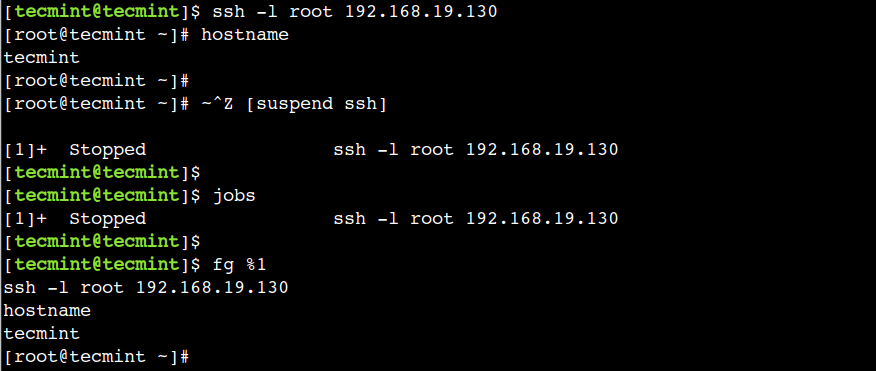
First, log in to the remote host and execute the hostname command:
$ ssh -l root 192.168.19.130 # hostname
Next, to suspend the current session first type tilde (~) character and then press the ctrl + z keys. It is important to note that the tilde (~) character will not be displayed on the stdout until we press ctrl + z.
Now, let’s verify that the session has been suspended:
$ jobs
Here, we can see that the current SSH session is running in the background.
Let’s resume the session again using the fg command and execute the hostname command:
$ fg %1
Terminate Frozen SSH Session
I’m sure you must have seen the frozen SSH sessions, which happen when the session gets interrupted by an unstable network. Here, we cannot abort the session using the exit command. However, we can terminate it using the "~ + ." key sequence.
First, log in to the remote host:
$ ssh -l root 192.168.19.130
Now use the "~ + ." key combination to terminate the current session.
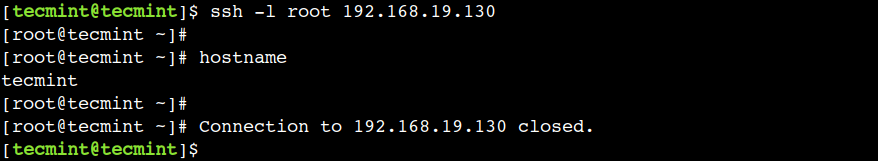
In this example, we can see that SSH shows the message – Connection to 192.168.19.130 closed.
List Supported Escape Sequence
One interesting thing is that there is an escape sequence to list all supported escape sequences. We can use the “~ + ?” escape sequence to list the supported escape sequences:
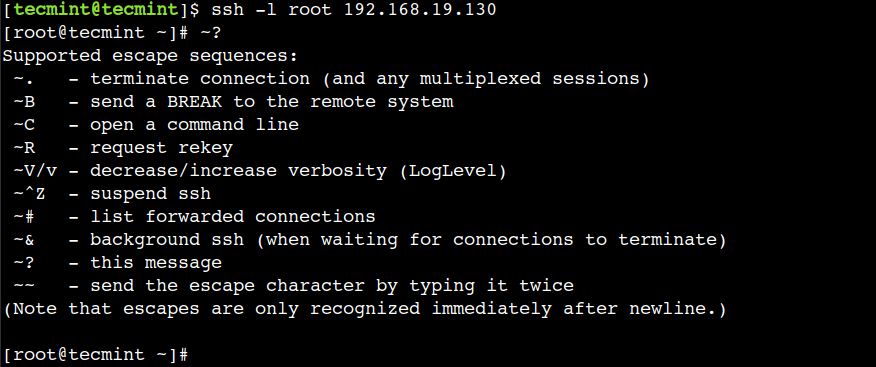
Here, we have to press enter key to come out from the help menu.
How to Configure SSH in Linux
In this section, we will discuss server-side configuration to harden the SSH server. SSH server stores all its configuration in /etc/ssh/sshd_config file. It is important to note that, root user access is required to update the SSH configuration.
Display SSH Banner
As a best practice, we should always display the banner before establishing an SSH connection. In some cases, it discourages unauthorized users from accessing remote hosts. Let’s see how to enable this setting step by step.
First, create a text file on a remote server with a warning message:
# vi /etc/banner.txt
Next, add the following banner message:
********************************************************************* Warning !!! You are trying to log in to techmint.com's server. All the activities on this server are monitored. Terminate the session immediately if you are not an authorized user. *********************************************************************
Next, open the /etc/ssh/sshd_config file and specify the file with the Banner directive:
Banner /etc/banner.txt
Now, restart the sshd service and terminate the session using the exit command:
# systemctl restart sshd # exit
Finally, verify the banner by logging in to the remote host:
$ ssh -l root 192.168.19.130
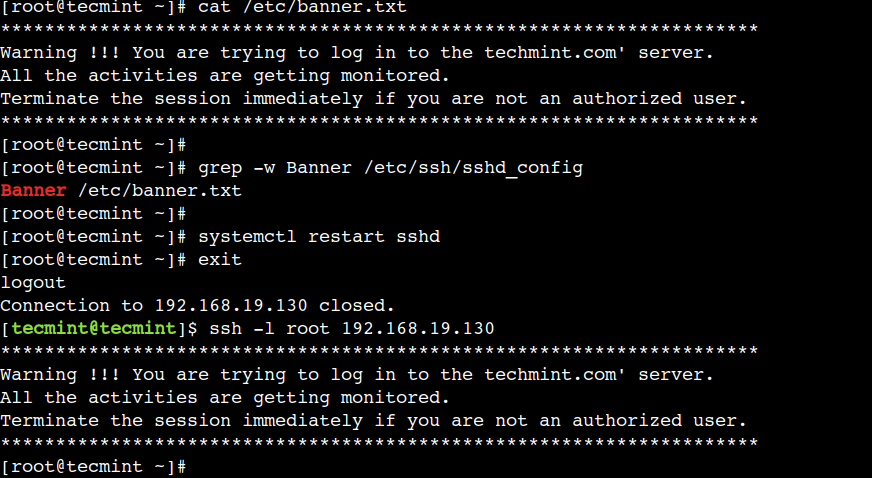
Here, we can that the server displays the SSH banner correctly.
Disable SSH Root Login
So far, we used the root user to access the remote host. However, this is against the principle of least privilege. In a production environment, root user access is always restricted to improve security.
We can use the PermitRootLogin directive to disable root user login.
First, open the /etc/ssh/sshd_config file and use the option no with the PermitRootLogin directive:
PermitRootLogin no
Now, restart the sshd service and terminate the session using the exit command:
# systemctl restart sshd # exit
Finally, verify this by creating a new SSH session:
$ ssh -l root 192.168.19.130
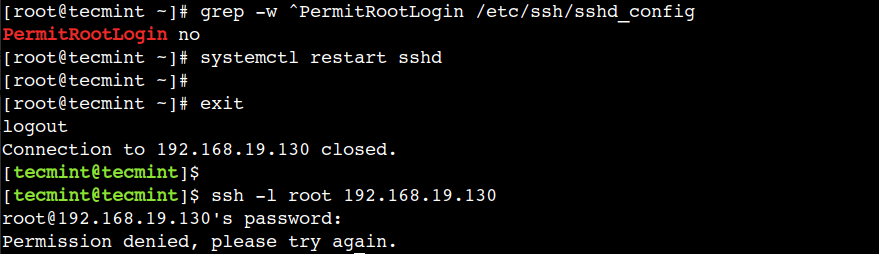
Here, we can observe that we cannot log in to the remote host with the root user. To allow root user login we can use the option yes with the same directive.
Change Default SSH Port
By default, SSH uses TCP port 22. However, we can configure SSH to run on a different port i.e. 8088.
First, open the /etc/ssh/sshd_config file and use the 8088 value with the Port directive:
Port 8088
Next, restart the sshd service and terminate the session:
# systemctl restart sshd # exit
Now, let’s login to the remote host:
$ ssh -p 8088 -l root 192.168.19.130
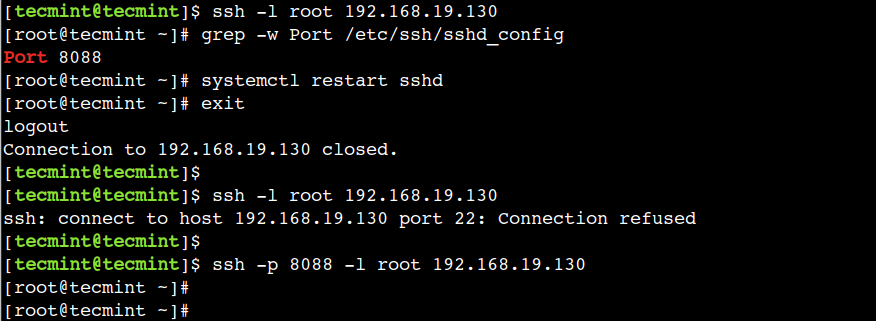
In this example, we have used the -p option to specify the port number.
In some cases, we have to perform a few other steps to allow communication on a non-default port. Such as identifying available ports, updating firewall rules, SELinux settings, etc.
In this article, we discussed the SSH protocol and its common use cases. Next, we discussed a few common options. Finally, we discussed some of the settings to secure the SSH server.
Do you know of any other best SSH command usage in Linux? Let us know your views in the comments below.