If you look up the word virtualize in a dictionary, you will find that it means “to create a virtual (rather than actual) version of something”. In computing, the term virtualization refers to the possibility of running multiple operating systems simultaneously and isolated one from another, on top of the same physical (hardware) system, known in the virtualization schema as host.

Through the use of the virtual machine monitor (also known as hypervisor), virtual machines (referred to as guests) are provided virtual resources (i.e. CPU, RAM, storage, network interfaces, to name a few) from the underlying hardware.
With that in mind, it is plain to see that one of the main advantages of virtualization is cost savings (in equipment and network infrastructure and in terms of maintenance effort) and a substantial reduction in the physical space required to accommodate all the necessary hardware.
Since this brief how-to cannot cover all virtualization methods, I encourage you to refer to the documentation listed in the summary for further details on the subject.
Please keep in mind that the present article is intended to be a starting point to learn the basics of virtualization in RHEL 7 using KVM (Kernel-based Virtual Machine) with command-line utilities, and not an in-depth discussion of the topic.
Verifying Hardware Requirements and Installing Packages
In order to set up virtualization, your CPU must support it. You can verify whether your system meets the requirements with the following command:
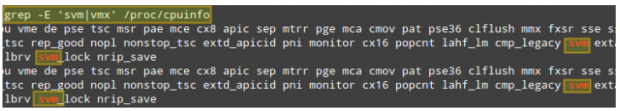
# grep -E 'svm|vmx' /proc/cpuinfo
In the following screenshot we can see that the current system (with an AMD microprocessor) supports virtualization, as indicated by svm. If we had an Intel-based processor, we would see vmx instead in the results of the above command.
In addition, you will need to have virtualization capabilities enabled in the firmware of your host (BIOS or UEFI).
Now install the necessary packages:
- qemu-kvm is an open source virtualizer that provides hardware emulation for the KVM hypervisor whereas qemu-img provides a command line tool for manipulating disk images.
- libvirt includes the tools to interact with the virtualization capabilities of the operating system.
- libvirt-python contains a module that permits applications written in Python to use the interface supplied by libvirt.
- libguestfs-tools: miscellaneous system administrator command line tools for virtual machines.
- virt-install: other command-line utilities for virtual machine administration.
# yum update && yum install qemu-kvm qemu-img libvirt libvirt-python libguestfs-tools virt-install
Once the installation completes, make sure you start and enable the libvirtd service:
# systemctl start libvirtd.service # systemctl enable libvirtd.service
By default, each virtual machine will only be able to communicate with the rest in the same physical server and with the host itself. To allow the guests to reach other machines inside our LAN and also the Internet, we need to set up a bridge interface in our host (say br0, for example) by,
1. adding the following line to our main NIC configuration (most likely /etc/sysconfig/network-scripts/ifcfg-enp0s3):
BRIDGE=br0
2. creating the configuration file for br0 (/etc/sysconfig/network-scripts/ifcfg-br0) with these contents (note that you may have to change the IP address, gateway address, and DNS information):
DEVICE=br0 TYPE=Bridge BOOTPROTO=static IPADDR=192.168.0.18 NETMASK=255.255.255.0 GATEWAY=192.168.0.1 NM_CONTROLLED=no DEFROUTE=yes PEERDNS=yes PEERROUTES=yes IPV4_FAILURE_FATAL=no IPV6INIT=yes IPV6_AUTOCONF=yes IPV6_DEFROUTE=yes IPV6_PEERDNS=yes IPV6_PEERROUTES=yes IPV6_FAILURE_FATAL=no NAME=br0 ONBOOT=yes DNS1=8.8.8.8 DNS2=8.8.4.4
3. finally, enabling packet forwarding by making, in /etc/sysctl.conf,
net.ipv4.ip_forward = 1
and loading the changes to the current kernel configuration:
# sysctl -p
Note that you may also need to tell firewalld that this kind of traffic should be allowed. Remember that you can refer to the article on that topic in this same series (Part 11: Network Traffic Control Using FirewallD and Iptables) if you need help to do that.



Is this available in PDF form at all?
@Johnson,
The whole RHCSA/RHCE series is available in PDF format as a ebook at $25 very soon, probably next week…
oh, cool. I’ll check back soon then. Thanks!
Thank you for the wonderful tutorials! When is part 16 etc going to be put on the website?
@Majid,
This was a 15-article series, so this is the last guide. Watch out for the coming RHCE series!
Once the VT/AMD-V bios settings are in place, it is never enough to just save and restart. For the features to become enabled, you need to power down the machine, and start it up again.